How Not To Get Hacked, Phished, or Fleeced
This is Finn’s outline that goes with the Security Basics workshop recorded on April 8th 2022 in the Orbital Command Terra Invest Strategies Discord server.

- Fakes and scammers, fake influencers, and fake listing contacts
- Fake sites impersonating the major protocols
- Fake QR Codes over the top of real ones
- People impersonating high level users in servers
- Scams having to do with password reset
- Preying on ego, psychology (money, sex, etc…)
SEED IS SEED. Most people aren’t getting hacked, they’re entering their info into fake sites or DM’s. It just sounds cooler to say “I got hacked.”
In order to not get fleeced, we need to understand how these scammers operate. How are some of these “hacks” perpetrated?
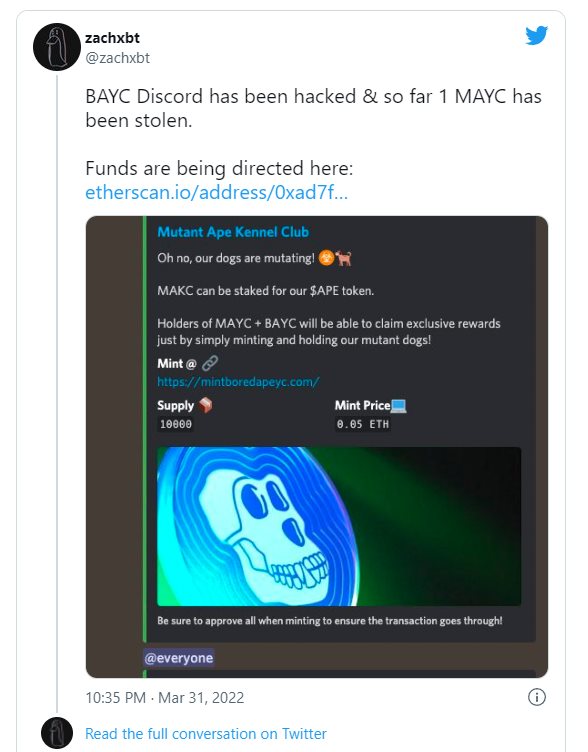
This example written about in Engadget on April 2nd involves some Discord mischief, and the most mischievous day of the year, April Fools.
Another example from the Eth blockchain was written about in the Hardware Zone on April 5th and involves a celeb not reading the transaction before he signed it. He will most likely never make that mistake again. Some lessons cost more than others.
Generally, the issue is PEBCAC. (Problem exists between chair and computer). Humans are the weakest link in this system. It’s much easier to socially engineer a human than it is to crack hardened, well made code.
Anchanted Art has a thread here about their experience with getting scammed. Here’s a few examples of what you might come across in the space.
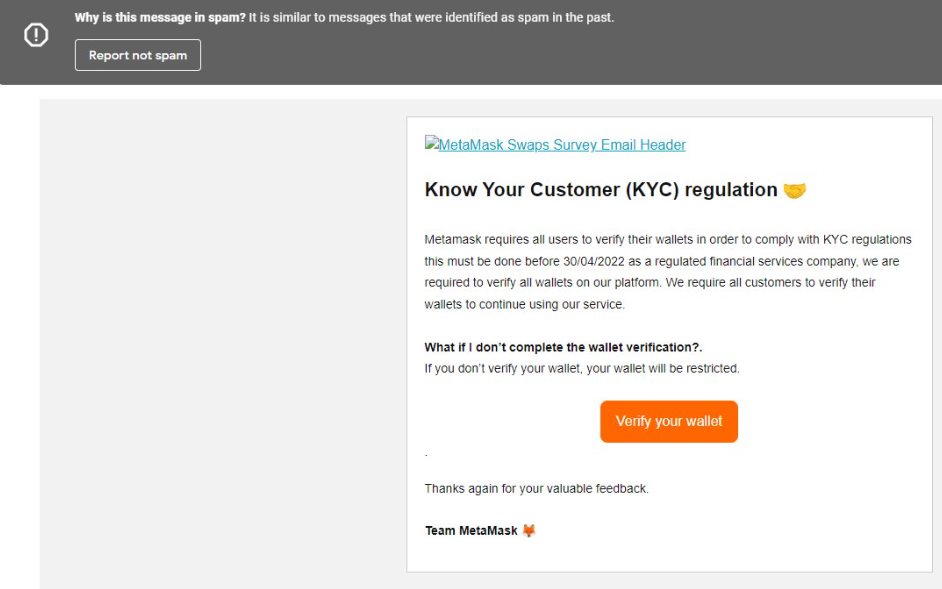
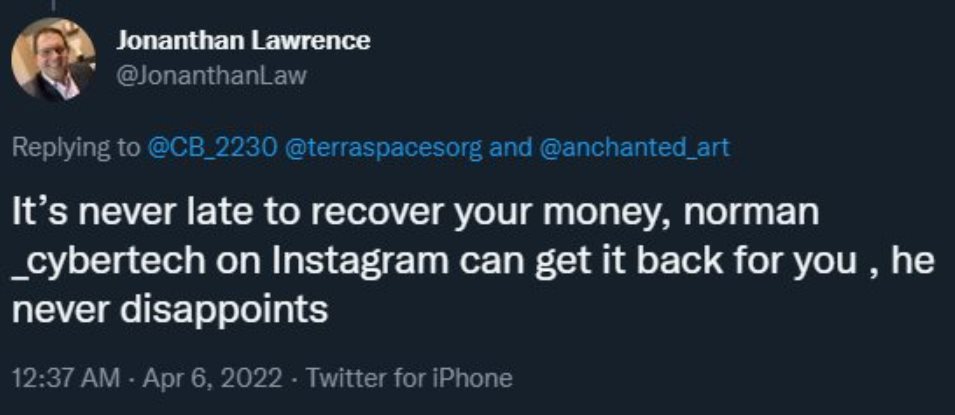
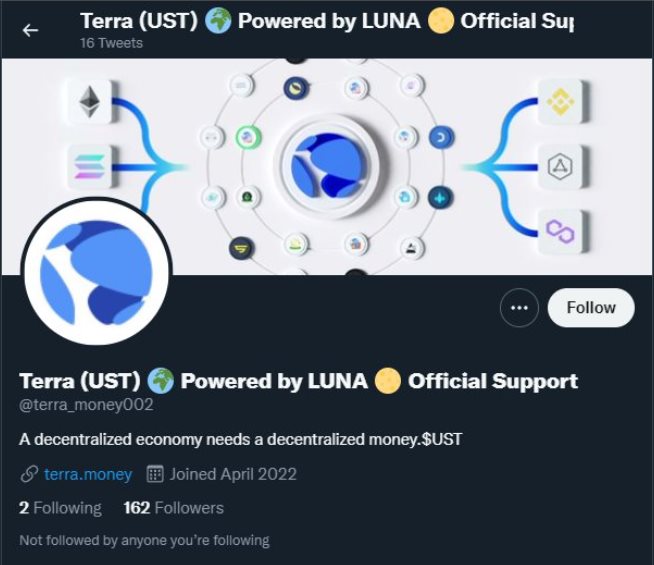
How Can You Be SAFU?
2FA… it can be a pain in the ass, but that’s how security goes. If it’s easy it’s most likely not secure. Don’t use the phone SMS 2FA either, that can be gotten around easier than the actual authenticator app by Google.
Use a different password on EVERY SITE. This is super important. Scammers rely on you using the same password on Twitter that you use for your bank. Don’t be the low hanging fruit.
Use a password generator, or use some sort of padding aka password haystacks.
Open Source VS Closed Source. Obviously trust no one (TNO) is the way, but unless you are building your own chips and coding your own OS, you have to inevitably trust someone. This is why I tend to lean more on the side of open source.
I can’t code, but I follow big brains that I trust (as much as you can trust anyone online) based on reputation and quality, and when they say something is as safe and as hardened as it can be, I trust them. Because I have no other choice.
The more eyeballs on code, the better. This is important for sniffing out things like back doored crypto algos. Why? Because this shit happens.

Elliptic Curve Cryptography (ECC) is a key-based technique for encrypting data. ECC focuses on pairs of public and private keys for decryption and encryption of web traffic.
Remember in 2013 when Edward Snowden told everyone about the backdoor in a particular set of ECC algorithms? I member. Wired also remembers.
You must always keep in mind these scammers prey on human psychology. They know everyone online wants to get rich for doing the least amount of work possible.
They know everyone online is looking for love in one form or another. These are things they exploit to get you thinking in a haze of dopamine and hopium.
No one is going to give you anything for free. Look before you leap, or crane before you click. Is that person really going to send you 2 bitcoin back after you send them 1? No.
Is that hot chick going to really use your credit card to buy herself a plane ticket to come be with you so you can live happily ever after? Definitely not…
By clicking on that link you randomly got in your email that said your package needs to be picked up and to click here to print out the information, are you really going to get a package you most likely didn’t even order in the first place? No.
Is the Nigerian prince really going to send you millions of dollars? No.
These are all just different versions of age old scams perpetrated throughout the centuries by snake oil salesmen and con artists.
These scams can happen to anyone at any time, via any vector. The worst is when people use disasters or other emergency situations to take advantage of people. Taking advantage of people at their most vulnerable is not nice.
Resources
- Perfect Passwords by GRC
- Password Haystack by GRC
- Off the Grid Paper Based Cypher by GRC
- Password Policies on Security Now
- Password Q&A on Security Now
- Personal Password Policy on Security Now
- Personal Password Policy Part 2 on SN
- Extrinsic Password Managers on SN
- Social-Engineer.com
- SE Blog on Impersonation
- SE Blog on Phishing
- Social Engineer Podcast